Crypto trading is thrilling, but it comes with its risks. Whether you’re a seasoned trader or just starting, securing your funds is essential. iCryptoX.com security is a top priority for anyone looking to protect their digital assets. This guide breaks down the platform’s top security features, provides practical tips for securing your account, and offers insights on how to make the most of iCryptoX.com security to keep your crypto safe.
Why iCryptoX.com Security Matters
Cryptocurrency is digital, which makes it vulnerable to online threats. In 2020, hackers stole $1.9 billion worth of crypto, with many of these attacks targeting exchanges that didn’t use robust security measures. Fortunately, iCryptoX.com security offers several tools to keep your funds safe. But your actions are just as important. In this guide, we’ll show you how to secure your account and protect your crypto assets on iCryptoX.com.
Key iCryptoX.com Security Features
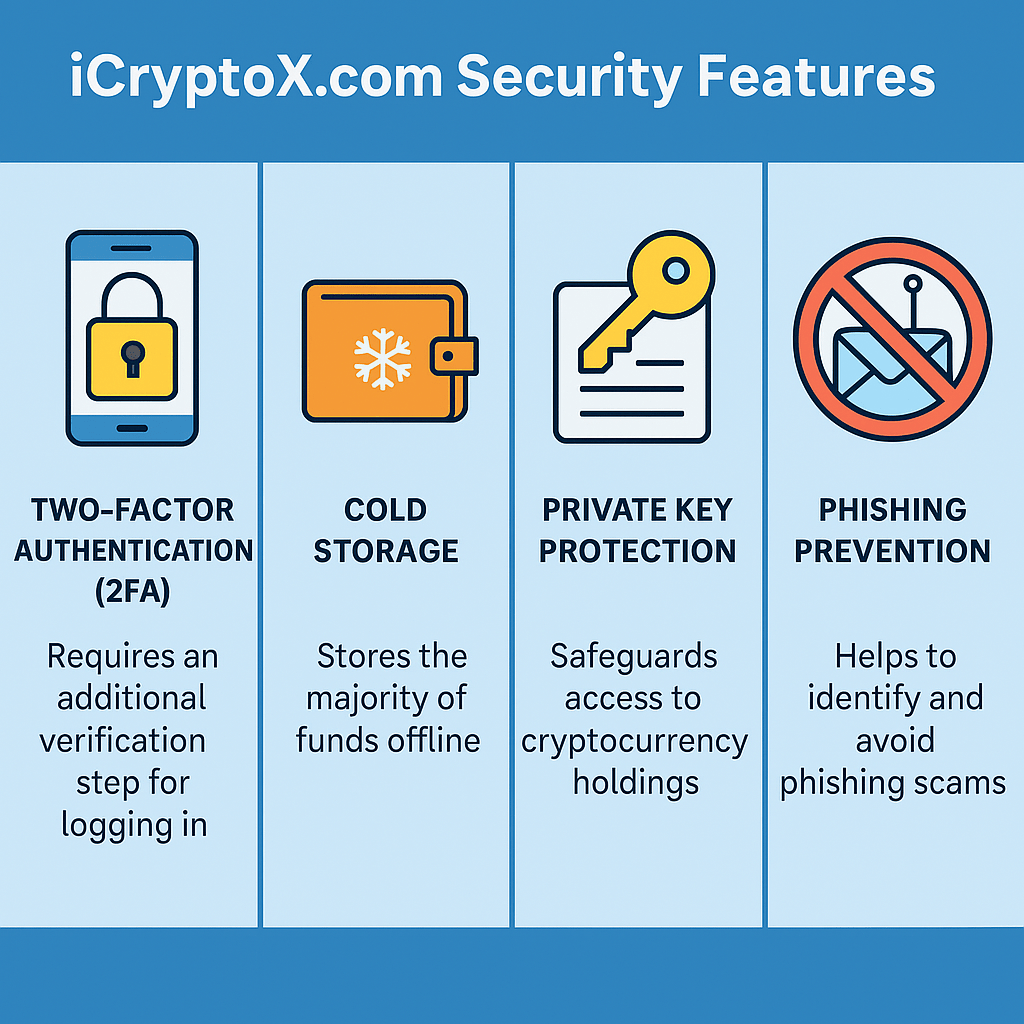
1. Two-Factor Authentication (2FA): Your First Line of Defense
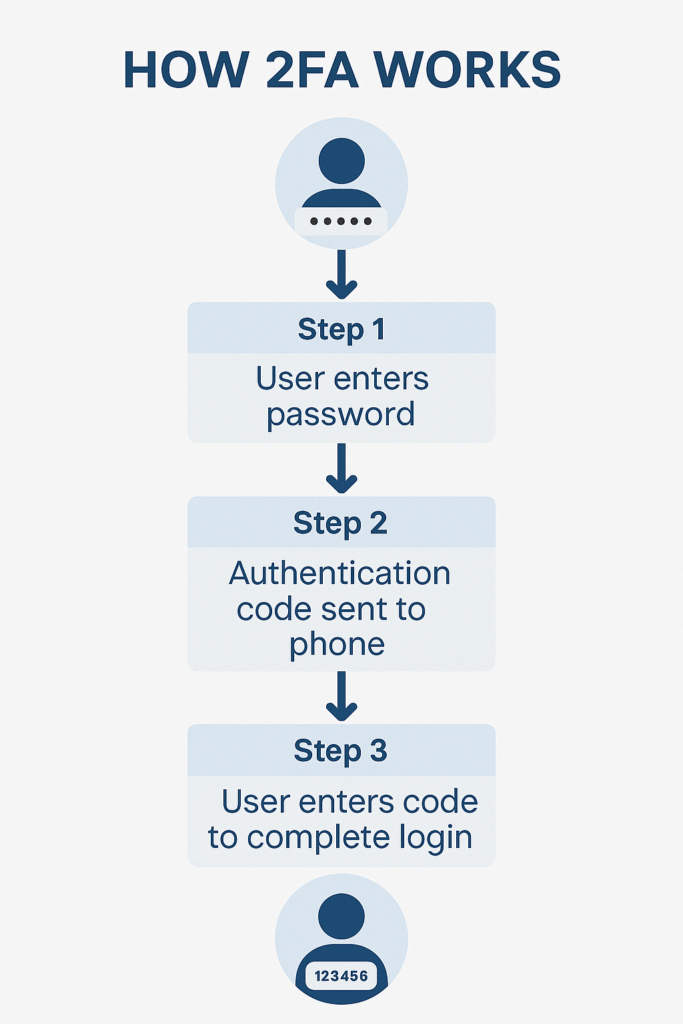
Two-factor authentication (2FA) is one of the simplest yet most effective ways to protect your iCryptoX.com security. By requiring a second layer of verification, typically a code sent to your phone or an app, 2FA makes it harder for hackers to access your account, even if they have your password.
Why 2FA Is Essential for iCryptoX.com Security:
Troy Hunt, a well-known security expert, says:
“Two-factor authentication is the easiest, most effective way to protect your online accounts. Even if your password is compromised, having that second layer of defense makes a huge difference.”
Google’s 2019 report revealed that enabling 2FA makes accounts 50 times less likely to be hacked. For securing your iCryptoX.com account, 2FA is an absolute must.
For more help setting up 2FA, follow Google’s official guide.
For more help setting up 2FA, follow Google’s official guide.
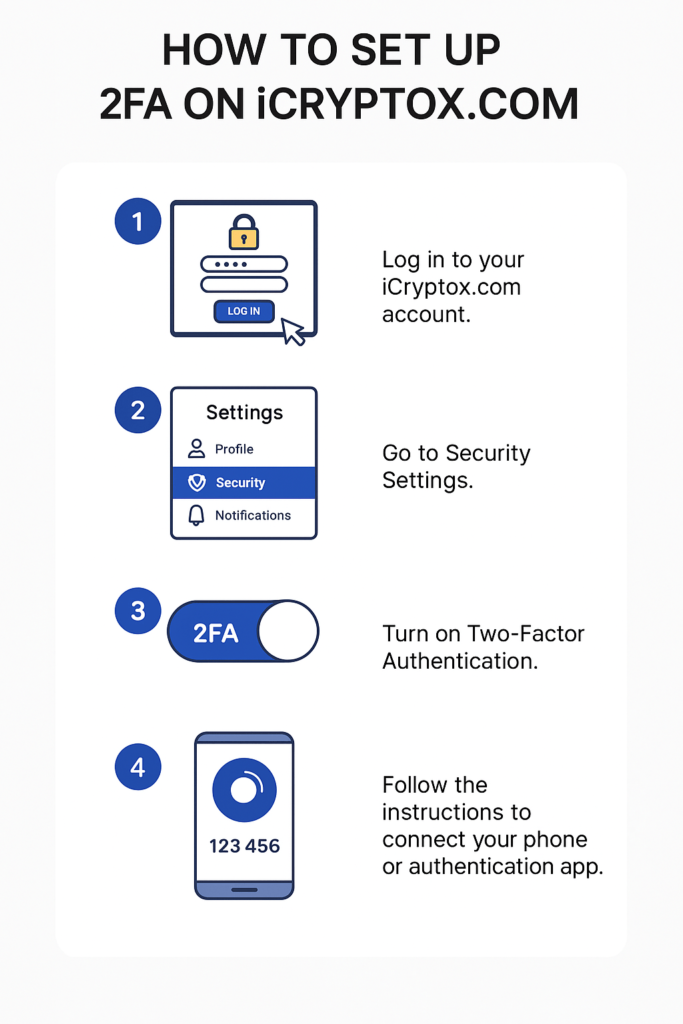
How to Set Up 2FA on iCryptoX.com:
- Log in to your iCryptoX.com account.
- Go to Security Settings.
- Turn on Two-Factor Authentication.
- Follow the instructions to connect your phone or authentication app.
2. Cold Storage: Safeguarding Your Crypto
Cold storage is when your cryptocurrency is stored offline, making it impossible for hackers to access it remotely. iCryptoX.com security uses cold storage for the majority of its user funds, ensuring that they remain safe even in the event of a platform breach.
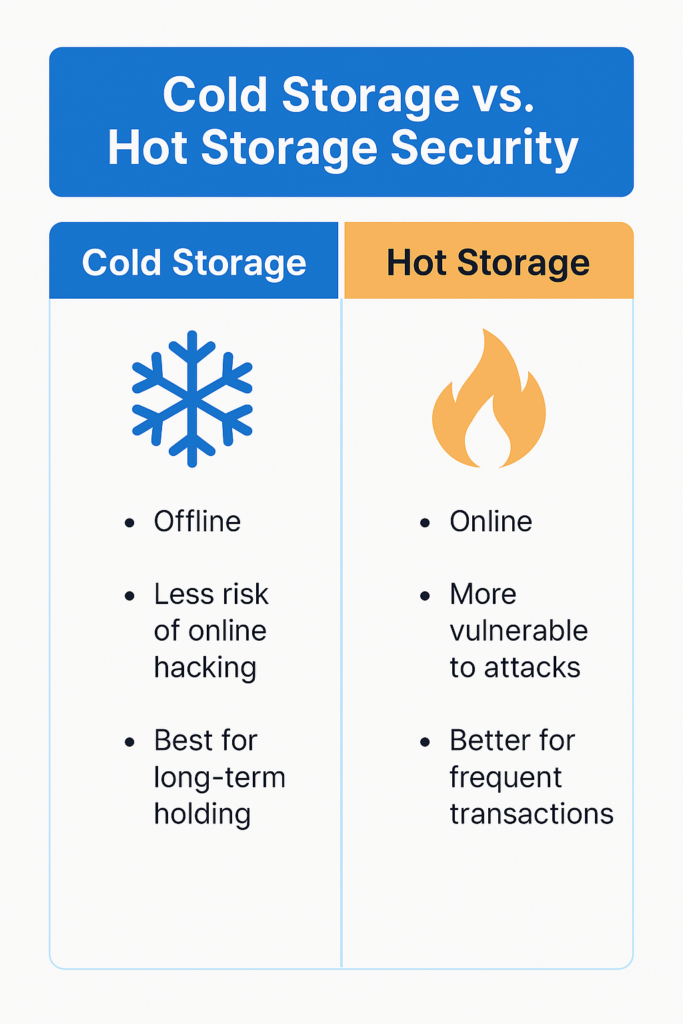
Why Cold Storage Is Critical for iCryptoX.com Security:
CipherTrace’s 2020 Crypto Crime Report showed that most crypto thefts occur on exchanges that fail to use cold storage. Storing crypto offline keeps it secure from online attacks. As Andreas M. Antonopoulos, a Bitcoin expert, says:
“Cold storage is the gold standard of crypto security. If you don’t control your private keys, you don’t control your cryptocurrency.”
Learn why cold storage is essential for crypto security according to industry experts at CoinTelegraph.
How to Use Cold Storage:
- Hardware Wallets: Devices like Ledger or Trezor store your crypto offline, providing secure long-term storage.
- Paper Wallets: Write down your private keys and store them in a safe place to avoid online threats.
Pro Tip: Always back up your cold storage in multiple locations. If you lose one backup, you’ll still be able to access your funds.
3. Phishing Scams: Be Cautious
Phishing scams are common ways hackers trick users into providing login credentials or private keys. These scams often appear to be official communications from iCryptoX.com, but they’re designed to steal your personal information.
Why Phishing Is a Risk to iCryptoX.com Security:
Kevin Mitnick, a former hacker turned security consultant, warns:
“Phishing remains one of the most effective methods that cybercriminals use to exploit human error. No matter how secure the technology is, the weakest link is often the user.”
According to Chainalysis, 30% of all crypto fraud in 2020 was linked to phishing scams. Protecting yourself from phishing is crucial for maintaining iCryptoX.com security.
Learn more about phishing attacks and crypto scams from Chainalysis.
How to Spot Phishing:
- Check the email address: Ensure that emails are from the official iCryptoX.com domain.
- Look for errors: Phishing emails often contain spelling mistakes or urgent requests.
- Don’t click on links: Instead, type iCryptoX.com directly into your browser.
4. Private Keys: Your Access to Crypto
Your private key is the only way to access your funds. If someone gains access to it, they can take your crypto. Properly protecting your private key is critical to maintaining iCryptoX.com security.
Why Private Key Security Is Essential:
As Jimmy Song, a Bitcoin educator, puts it:
“Not your keys, not your coins. If you don’t control your private keys, you don’t control your cryptocurrency.”
Without your private key, you lose access to your assets, making it vital to store them safely.
Best Practices for Storing Private Keys:
- Cold Storage: Store your private keys in hardware wallets or encrypted USB drives.
- Backup: Write your private keys on paper and keep them in a safe place, like a fireproof safe.
Statistic: In 2013, a user accidentally threw away a paper wallet with 7,500 BTC. That’s worth millions today. This illustrates the importance of securing your private keys.
5. Regular Monitoring: Stay One Step Ahead
Even with 2FA and cold storage in place, it’s important to monitor your account for suspicious activity. Actively reviewing your account can help you detect unauthorized actions early.
Why Monitoring Helps Your iCryptoX.com Security:
Bruce Schneier, a leading security expert, says:
“The best way to avoid being hacked is to assume you’re going to be hacked. So, you should regularly monitor your accounts to quickly spot and deal with unauthorized activity.”
How to Monitor Your Account:
- Set up alerts: Enable email or SMS notifications for logins and transactions.
- Review transaction history: Regularly check for any unauthorized withdrawals.
- Use IP Whitelisting: Limit access to specific devices or locations for extra protection.
Frequently Asked Questions About iCryptoX.com Security
1. Is iCryptoX.com Safe to Use?
Yes. iCryptoX.com uses cold storage, two-factor authentication (2FA), and encryption to protect your funds. However, you should always enable these features and be cautious of phishing attempts.
2. What Should I Do If My Account Is Compromised?
- Change your password immediately.
- Enable 2FA if you haven’t already.
- Review your account for unauthorized transactions.
- Contact iCryptoX.com support.
3. How Do I Protect My Private Keys?
- Store them in cold storage (hardware wallets or encrypted USB drives).
- Back them up in secure locations, like a safe or safety deposit box.
Final Thoughts on iCryptoX.com Security
Securing your crypto is a shared responsibility. iCryptoX.com offers great security features, but it’s up to you to actively use them. Enable 2FA, use cold storage, watch out for phishing scams, and monitor your account regularly. By following these steps, you can enjoy a secure trading experience on iCryptoX.com.
Key Takeaways:
- Enable Two-Factor Authentication (2FA) for added protection.
- Store your crypto in cold storage to keep it safe.
- Keep your private keys offline and secure.
- Stay cautious of phishing scams—always verify links and emails.
- Regularly monitor your account for suspicious activity.
By following these practices, you can confidently trade and secure your assets on iCryptoX.com.
About the Author
I’ve been involved in the cryptocurrency space for several years and understand how critical security is. This guide is based on my personal experience and research into the best security practices for crypto traders.
For more information, visit iCryptoX.com’s security page.
Want to stay up-to-date with breaking news, trends, and insightful articles? Visit our homepage at HeadNewsNow to get the latest updates delivered straight to you!

